In Part 1 I showed you how to use IKeyMan to set up your SSL keys database.
Now in Part 2 we will configure IHS to actually use your keys and to use TLS (SSL).
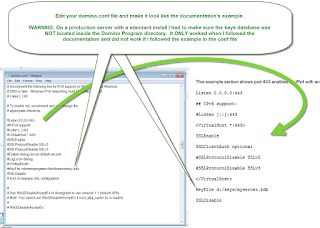
Since you’ve already set up IBM HTTP Server on your Domino 9 server, all you need to do now is edit the domino.conf file and tell IHS to start using SSL.
The Domino documentation is perfect here, too. I followed their steps to the letter and it worked. When I deviated, it didn’t work so <GOODADVICE>save your deviation and creativity until you have the basics working then tweak</GOODADVICE>.
Once you have edited your domino.conf file, restart your Domino server and see what happens.
If you see this, it didn’t work and you need to go back and retrace your steps because something is missing.
If you see the normal startup in your console then rush over to your browser and visit your site using https://…. Then be glad because you’re now using the best encryption available to your Domino server!
And now a little bit of Tweaking…
Let’s say you want to enable Client Certificates or only allow specific SSL ciphers to be used. There all kinds of thing you can change on you IHS to make it work the way you want.
Take a look here (not sure if this is the most official list but do some Googling).
Here are a couple of examples.